Find the latest threat intelligences direct from AhnLab’s security experts
Chat feature was not able to connect when security researchers at AhnLab analyzed the relevant ransomware. Elaborate designs Some ransomware suspiciously display irregular designs, whereas many ransomware and variants poorly. AhnLab ASEC has gathered Excel files that leak user info using malicious macro. The Excel file prompts the user to run macro, and when macro is run, it re-runs the Excel document that contains a court decision stating that the user ‘must pay a fine for abetting a breach on the Act On Door-To-Door Sales, etc. To make it difficult for the users to realize that their PC is infected.
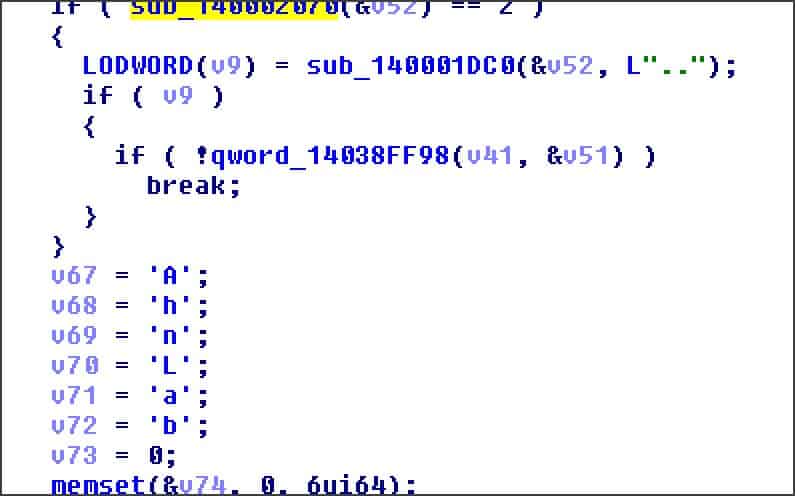
Threat Analysis_Operation Shadow Force
Operation Shadow Force
This analysis report will examine Operation Shadow Force that had been hidden behind legitimate certificates for the last seven years.
DownLoadThreat Analysis
Five Malicious Sextortion Apps
This analysis report will examine the top five malicious applications being used for sextortion scams.
DownLoad

Issue Report
Ahnlab Ransomware
The Evolution of Magniber Ransomware This analysis report will examine the recent malicious activities of Magniber ransomware from changes in exploited vulnerability to shellcode. DownLoad | |
Sour Lemon Duck: PowerShell Malware Exploiting SMB Vulnerability This analysis report presents the kill-chain, primary functions, and internal proliferation methods of Lemon Duck in full detail. DownLoad | |
Operation Kabar Cobra: Tenacious cyber-espionage by Kimsuky This report describes the latest attacks by Kimsuky Group including main methods, and changes in their purpose and targets. DownLoad | |
Full Discloser of Andariel, a Subgroup of Lazarus Threat Group This report describes the several cyberattacks by Andariel Threat Group including main methods, and changes in their purpose and targets DownLoad | |
Ghosts Dwelling in the USB Memory This analysis report will examine the the malware that has been dwelling in the USB memory during the last decade. DownLoad | |
Detailed Analysis of Red Eyes Hacking Group This report takes a closer look at the main activities of Red Eyes and another group that may be affiliated with it. DownLoad | |
Analysis Report on Attacks Targeting South Korea This report shows attacks targeting South Korea; attack method and hacking groups. DownLoad | |
Targeted Attacks on Defense Industry This report presents analysis of attacks on defense industry which can be serious concerns to national security. DownLoad |